This is the mobile-friendly web version of the original article.

31 January 2022
PIN Number
PIN-20220131-001
Potential for Malicious Cyber Activities to Disrupt the 2022 Beijing Winter Olympics and Paralympics
Summary
The FBI is warning entities associated with the February 2022 Beijing Winter Olympics and March 2022 Paralympics that cyber actors could use a broad range of cyber activities to disrupt these events. These activities include distributed denial of service (DDoS) attacks, ransomware, malware, social engineering, data theft or leaks, phishing campaigns, disinformation campaigns, or insider threats, and when successful, can block or disrupt the live broadcast of the event, steal or leak sensitive data, or impact public or private digital infrastructure supporting the Olympics. Additionally, the FBI warns Olympic participants and travelers of potential threats associated with mobile applications developed by untrusted vendors. The download and use of applications, including those required to participate or stay in country, could increase the opportunity for cyber actors to steal personal information or install tracking tools, malicious code, or malware1 . The FBI urges all athletes to keep their personal cell phones at home and use a temporary phone while at the Games. The National Olympic Committees in some Western countries are also advising their athletes to leave personal devices at home or use temporary
1 For more information on the malware risk associated with government-mandated software, please see FBI FLASH AC-000129-TT, disseminated on 23 July 2020, titled “Tactics, Techniques, and Procedures Associated with Malware within Chinese Government-Mandated Tax Software.”
phones due to cybersecurity concerns at the Games. The FBI to date is not aware of any specific cyber threat against the Olympics, but encourages partners to remain vigilant and maintain best practices in their network and digital environments.
Threat
As we mentioned in PIN 20210719-001, large, high-profile events provide an opportunity for criminal and nation-state cyber actors to make money, sow confusion, increase their notoriety, discredit adversaries, and advance ideological goals. Due to the ongoing COVID-19 pandemic, no foreign spectators will be allowed to attend the Olympics or Paralympics. Spectators will be reliant on remote streaming services and social media throughout the duration of the Games. Adversaries could use social engineering and phishing campaigns leading up to and during the event to implant malware to disrupt networks broadcasting the event. Cyber actors could use ransomware or other malicious tools and services available for purchase to execute DDoS attacks against Internet service providers and television broadcast companies to interrupt service during the Olympics. Similarly, actors could target the networks of hotels, mass transit providers, ticketing services, event security infrastructure or similar Olympic support functions.
For example, during the 2020 Tokyo Olympics and Paralympics, the NTT Corporation––which provided its services for the Tokyo Olympic & Paralympic Games––revealed there were more than 450 million attempted cyber-related incidents during the event, though none were successful due to cybersecurity measures in place. While there were no major cyber disruptions, the most popular attack methods used were malware, email spoofing, phishing and the use of fake websites and streaming services designed to look like official Olympic service providers.
In addition, the use of new digital infrastructure and mobile applications, such as digital wallets or applications that track COVID testing or vaccination status, could also increase the opportunity for cyber actors to steal personal information or install tracking tools, malicious code, or malware. Athletes will be required to use the smartphone app, MY2022, which will be used to track the athletes’ health and travel data.
During the 2018 PyeongChang Winter Olympics, Russian cyber actors conducted a destructive cyber attack against the opening ceremony, enabled through spearphishing campaigns and malicious mobile applications.
Recommendations
- Ensure anti-virus and anti-malware software is enabled and signature definitions are updated regularly in a timely manner. Well-maintained anti-virus software may prevent use of commonly deployed attacker tools that are delivered via spear-phishing.
- Adopt threat reputation services at the network device, operating system, application, and email service levels. Reputation services can be used to detect or prevent low-reputation email addresses, files, URLs, and IP addresses used in spear-phishing attacks.
- If your organization’s information was previously compromised, the FBI recommends considering how any data exfiltrated could be leveraged to conduct further malicious activity against your network, and take appropriate measures to ensure security mechanisms are in place.
- If your organization is employing certain types of software and appliances referenced in the aforementioned CVEs, the FBI recommends patching for those vulnerabilities.
- Review the Tactics, Techniques, and Procedures in the referenced table and take steps to ensure you can identify and defend against malicious activity by this actor.
- Consider reputable hosting services for websites and content management systems (CMS), if you need assistance in configuring and maintaining your external facing applications.
- Consider employing a Web Application Firewall (WAF) to block inbound malicious traffic.
- Disable Content Management Systems features if they are not needed, and configure them to:
- Disable remote file editing
- Restrict file execution to specific directories
- Limit login attempts
- Review the logs generated by security devices for signs that your organizations external networks are being scanned for vulnerabilities.
Reporting Notice
The FBI encourages recipients of this document to report information concerning suspicious or criminal activity to their local FBI field office. Field office contacts can be identified at www.fbi.gov/contact-us/fieldoffices. When available, each report submitted should include the date, time, location, type of activity, number of people, and type of equipment used for the activity, the name of the submitting company or organization, and a designated point of contact.
The FBI also notes the Department of State’s Rewards for Justice Program is offering up to $10 million for information leading to the identification or location of Emennet-associated cyber actors Seyyed Mohammad Hosein Musa Kazemi and Sajjad Kashian:
- https://rewardsforjustice.net/terrorist-rewards/seyyed-kazemi/
- https://rewardsforjustice.net/terrorist-rewards/sajjad-kashian/
Administrative Note
This product is marked TLP:WHITE. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction.
Your Feedback Regarding this Product is Critical
Please take a few minutes to send us your feedback. Your feedback submission may be anonymous. We read each submission carefully, and your feedback will be extremely valuable to the FBI. Feedback should be specific to your experience with our written products to enable the FBI to make quick and continuous improvements to these products. Feedback may be submitted online here: https://www.ic3.gov/PIFSurvey
Appendix A
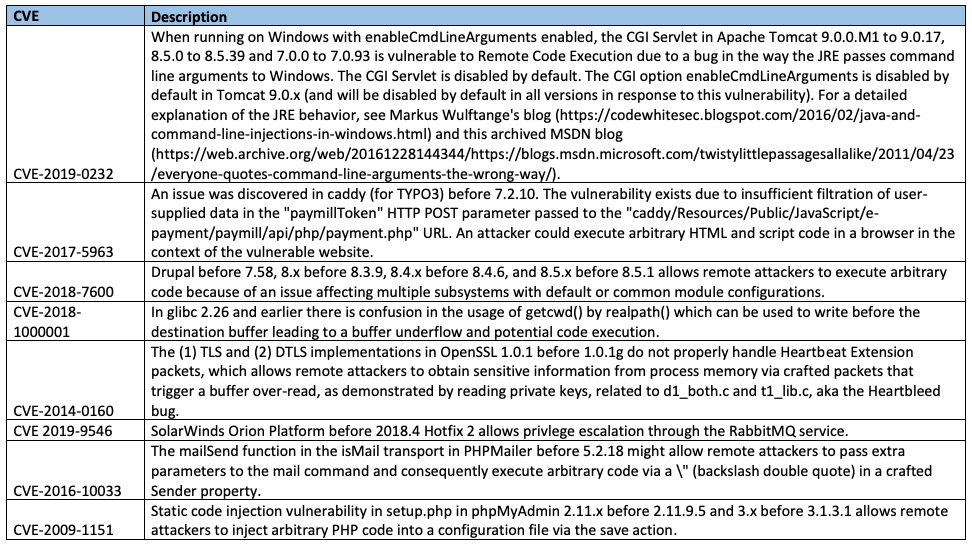


Source: National Vulnerability Database (nvd.nist.gov)