THREAT OVERVIEWS FOR 2021
BUSINESS EMAIL COMPROMISE (BEC)
In 2021, the IC3 received 19,954 Business Email Compromise (BEC)/ Email Account Compromise (EAC) complaints with adjusted losses at nearly $2.4 billion. BEC/EAC is a sophisticated scam targeting both businesses and individuals performing transfers of funds. The scam is frequently carried out when a subject compromises legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
As fraudsters have become more sophisticated and preventative measures have been put in place, the BEC/EAC scheme has continually evolved in kind. The scheme has evolved from simple hacking or spoofing of business and personal email accounts and a request to send wire payments to fraudulent bank accounts. These schemes historically involved compromised vendor emails, requests for W-2 information, targeting of the real estate sector, and fraudulent requests for large amounts of gift cards. Now, fraudsters are using virtual meeting platforms to hack emails and spoof business leaders’ credentials to initiate the fraudulent wire transfers. These fraudulent wire transfers are often immediately transferred to cryptocurrency wallets and quickly dispersed, making recovery efforts more difficult.
The COVID-19 pandemic and the restrictions on in-person meetings led to increases in telework or virtual communication practices. These work and communication practices continued into 2021, and the IC3 has observed an emergence of newer BEC/EAC schemes that exploit this reliance on virtual meetings to instruct victims to send fraudulent wire transfers. They do so by compromising an employer or financial director’s email, such as a CEO or CFO, which would then be used to request employees to participate in virtual meeting platforms. In those meetings, the fraudster would insert a still picture of the CEO with no audio, or a “deep fake” audio through which fraudsters, acting as business executives, would then claim their audio/video was not working properly. The fraudsters would then use the virtual meeting platforms to directly instruct employees to initiate wire transfers or use the executives’ compromised email to provide wiring instructions.
IC3 RECOVERY ASSET TEAM
The Internet Crime Complaint Center’s Recovery Asset Team (RAT) was established in February 2018 to streamline communication with financial institutions and assist FBI field offices with the freezing of funds for victims who made transfers to domestic accounts under fraudulent pretenses.

The RAT functions as a liaison between law enforcement and financial institutions supporting statistical and investigative analysis.
Goals of RAT-Financial Institution Partnership
- Assist in the identification of potentially fraudulent accounts across the sector.
- Remain at the forefront of emerging trends among financial fraud schemes.
- Foster a symbiotic relationship in which information is appropriately shared.
Guidance for BEC Victims
- Contact the originating financial institution as soon as fraud is recognized to request a recall or reversal and a Hold Harmless Letter or Letter of Indemnity.
- File a detailed complaint with www.ic3.gov. It is vital the complaint contain all required data in provided fields, including banking information.
- Visit www.ic3.gov for updated PSAs regarding BEC trends as well as other fraud schemes targeting specific populations, like trends targeting real estate, pre-paid cards, and W-2s, for example.
- Never make any payment changes without verifying the change with the intended recipient; verify email addresses are accurate when checking email on a cell phone or other mobile device
5 Accessibility description: Image shows the different stages of a complaint in the RAT process.
RAT SUCCESSES6
The IC3 RAT has proven to be a valuable resource for field offices and victims. The following are three examples of the RAT’s successful contributions to investigative and recovery efforts:
Philadelphia In December 2021, the IC3 received a complaint filed by a victim roadway commission regarding a wire transfer of more than $1.5 million to a fraudulent U.S. domestic bank account. The IC3 RAT quickly notified the recipient financial institution of the fraudulent account by initiating the financial fraud kill chain. Collaboration between the IC3 RAT, the recipient financial institution, and the Philadelphia Field office resulted in learning the subject quickly depleted the wired funds from the original account into two separate accounts held at the same institution. The financial institution was able to quickly identify the second-hop accounts and freeze the funds, making a full recovery possible.
Memphis In June 2021, the IC3 received a complaint filed by a victim law office regarding a wire transfer of more than $198k to a fraudulent U.S. domestic account. IC3 RAT collaboration with the Memphis Field Office and the recipient financial institution resulted in learning the domestic account was a correspondent account for a fraudulent account in Nigeria. IC3 RAT immediately initiated the international FFKC to FinCEN and LEGAT Abuja, which resulted in freezing the full wired amount. The victim forwarded a note of gratitude for all the work put into their case.
Albany In October 2021, the IC3 received a complaint filed by a victim of a tech support scam where an unauthorized wire transfer of $53k was sent from their account to a U.S. domestic custodial account held by a cryptocurrency exchange (CE). The IC3 RAT immediately notified the recipient financial institution and collaborated with the CE that held the account. With the knowledge that funds sent to cryptocurrency accounts will be depleted to crypto faster than the usual wire transfer gets depleted, the immediate efforts of initiating the financial fraud kill chain with the CE resulted in the freezing of the funds in the custodial account before they could be depleted to purchase or withdraw cryptocurrency. Further collaboration with the domestic financial institution and the Albany Field Office confirmed the funds were frozen in the account, making a full recovery possible.
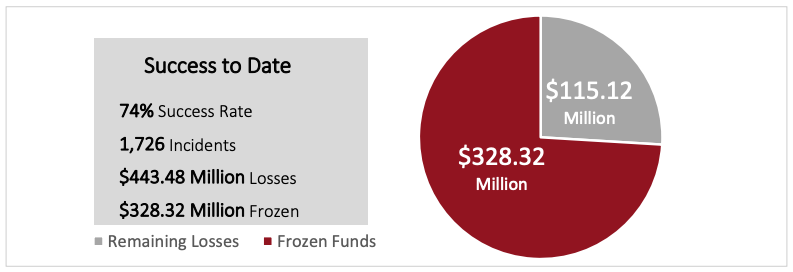
6 Accessibility description: Image shows Success to Date to include 74% Success Rate; 1,726 Incidents; $433.48 Million in Losses; and $328.32. Million Frozen.
CONFIDENCE FRAUD / ROMANCE SCAMS7
Confidence Fraud/Romance scams encompass those designed to pull on a victim’s “heartstrings.” In 2021, the IC3 received reports from 24,299 victims who experienced more than $956 million in losses to Confidence Fraud/Romance scams. This type of fraud accounts for the third highest losses reported by victims.

Romance scams occur when a criminal adopts a fake online identity to gain a victim’s affection and confidence. The scammer uses the illusion of a romantic or close relationship to manipulate and/or steal from the victim. The criminals who carry out Romance scams are experts at what they do and will seem genuine, caring, and believable. The scammer’s intention is to quickly establish a relationship, endear himself/herself to the victim, gain trust, and eventually ask for money. Scammers may propose marriage and make plans to meet in person, but that will never happen. Scam artists often say they are in the military, or a trades-based industry engaged in projects outside the U.S. That makes it easier to avoid meeting in person—and more plausible when they request money be sent overseas for a medical emergency or unexpected legal fee. Grandparent Scams also fall into this category, where criminals impersonate a panicked loved one, usually a grandchild, nephew, or niece of an elderly person. The loved one claims to be in trouble and needs money immediately.
Con artists are present on most dating and social media sites. In 2021, the IC3 received thousands of complaints from victims of online relationships resulting in sextortion or investment scams.
- Sextortion occurs when someone threatens to distribute your private and sensitive material if their demands are not met. In 2021, the IC3 received more than 18,000 sextortion-related complaints, with losses over $13.6 million. Please see the September 2021 IC3 PSA on Sextortion for more information.8
- Many victims of Romance scams also report being pressured into investment opportunities, especially using cryptocurrency. In 2021, the IC3 received more than 4,325 complaints, with losses over $429 million, from Confidence Fraud/Romance scam victims who also reported the use of investments and cryptocurrencies, or “pig butchering” –so named because victims’ investment accounts are fattened up before draining, much a like a pig before slaughter. Additional information on “pig butchering” can be found in the September 2021 IC3 PSA I-091621-PSA.9
7 Accessibility description: Chart shows Confidence Fraud/Romance Scam Victim by Reported Age Group. Under 20 2%; 20-29 10%; 30-39 15%; 40-49 15%; 50-59 16%; Over 60 32%
8 FBI Warns about an Increase in Sextortion Complaints. https://www.ic3.gov/Media/Y2021/PSA210902
9 Scammers Defraud Victims of Millions of Dollars in New Trend in Romance Scams.
CRYPTOCURRENCY (VIRTUAL CURRENCY)
In 2021, the IC3 received 34,202 complaints involving the use of some type of cryptocurrency, such as Bitcoin, Ethereum, Litecoin, or Ripple. While that number showed a decrease from 2020’s victim count (35,229), the loss amount reported in IC3 complaints increased nearly seven-fold, from 2020’s reported amount of $246,212,432, to total reported losses in 2021 of more than $1.6 billion.
Initially worth only fractions of pennies on the dollar, several cryptocurrencies have seen their values increase substantially, sometimes exponentially. Once limited to hackers, ransomware groups, and other denizens of the “dark web,” cryptocurrency is becoming the preferred payment method for all types of scams – SIM swaps, tech support fraud, employment schemes, romance scams, even some auction fraud. It is extremely pervasive in investment scams, where losses can reach into the hundreds of thousands of dollars per victim. The IC3 has noted the following scams particularly using cryptocurrencies.
- Cryptocurrency ATMs: Automated Teller Machines (ATMs) used to purchase cryptocurrency are popping up everywhere. Regulations on the machines are lax and purchases are almost instantaneous and irreversible, making this payment method lucrative to criminals. In 2021, the IC3 received more than 1,500 reports of scams using crypto ATMs, with losses of approximately $28 million. The most common scams reported were Confidence Fraud/Romance, Investment, Employment, and Government Impersonation. Read more about crypto ATM scams in IC3 PSA I110421-PSA.10
- Cryptocurrency support impersonators: Increasingly, crypto owners are falling victim to scammers impersonating support or security from cryptocurrency exchanges. Owners are alerted of an issue with their crypto wallet and are convinced to either give access to their crypto wallet or transfer the contents of their wallet to another wallet to “safeguard” the contents. Crypto owners are also searching online for support with their cryptocurrencies. Owners contact fake support numbers located online and are convinced to give up login information or control of their crypto accounts.
- Many victims of Romance scams also report being pressured into investment opportunities, especially using cryptocurrency. In 2021, the IC3 received more than 4,325 complaints, with losses over $429 million, from Confidence Fraud/Romance scam victims who also reported the use of investments and cryptocurrencies, or “pig butchering.” The scammer’s initial contact is typically made via dating apps and other social media sites. The scammer gains the confidence and trust of the victim, and then claims to have knowledge of cryptocurrency investment or trading opportunities that will result in substantial profits.
https://www.ic3.gov/Media/Y2021/PSA210916 10 The FBI Warns of Fraudulent Schemes Leveraging Cryptocurrency ATMs and QR Codes to Facilitate Payment https://www.ic3.gov/Media/Y2021/PSA211104
RANSOMWARE 11
In 2021, the IC3 received 3,729 complaints identified as ransomware with adjusted losses of more than $49.2 million. Ransomware is a type of malicious software, or malware, that encrypts data on a computer, making it unusable. A malicious cyber criminal holds the data hostage until the ransom is paid. If the ransom is not paid, the victim’s data remains unavailable. Cyber criminals may also pressure victims to pay the ransom by threatening to destroy the victim’s data or to release it to the public.
Ransomware tactics and techniques continued to evolve in 2021, which demonstrates ransomware threat actors’ growing technological sophistication and an increased ransomware threat to organizations globally. Although cyber criminals use a variety of techniques to infect victims with ransomware, phishing emails, Remote Desktop Protocol (RDP) exploitation, and exploitation of software vulnerabilities remained the top three initial infection vectors for ransomware incidents reported to the IC3. Once a ransomware threat actor has gained code execution on a device or network access, they can deploy ransomware. Note: these infection vectors likely remain popular because of the increased use of remote work and schooling starting in 2020 and continuing through 2021. This increase expanded the remote attack surface and left network defenders struggling to keep pace with routine software patching.12
Immediate Actions You Can Take Now to Protect Against Ransomware:
- Update your operating system and software.
- Implement user training and phishing exercises to raise awareness about the risks of suspicious links and attachments.
- If you use Remote Desktop Protocol (RDP), secure and monitor it.
- Make an offline backup of your data.
***
Ransomware and Critical Infrastructure Sectors In June 2021, the IC3 began tracking reported ransomware incidents in which the victim was a member of a critical infrastructure sector. There are 16 critical infrastructure sectors whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on our security, national economy, public health or safety, or any combination thereof.
11 Accessibility description: Image shows actions you can Take to Protect Against Ransomware: Update your operating system. Implement user training and phishing exercises to raise awareness, secure and monitor Remote Desktop Protocol (DDP) if used, and make an offline backup of our data.
12 2021 Trends Show Increased Globalized Threat of Ransomware.
https://www.ic3.gov/Media/News/2022/220209.pdf
In October 2021, the IC3 posted a Joint Cybersecurity Advisory (CSA) to ic3.gov regarding ongoing cyber threats to U.S. Water and Wastewater Systems. In September 2021, the IC3 posted a Private Industry Notification (PIN) which warned that ransomware attacks targeting the Food and Agriculture sector disrupt operations, cause financial loss, and negatively impact the food supply chain. In May 2021, the IC3 posted an FBI Liaison Alert System (FLASH) report that advised the FBI identified at least 16 CONTI ransomware attacks targeting US Healthcare and First Responder networks, including law enforcement agencies, emergency medical services, 9-1-1 dispatch centers, and municipalities within the last year. And in March 2021, the IC3 posted a FLASH warning that FBI reporting indicated an increase in PYSA ransomware targeting education institutions in 12 US states and the United Kingdom.
The IC3 received 649 complaints that indicated organizations belonging to a critical infrastructure sector were victims of a ransomware attack. Of the 16 critical infrastructure sectors, IC3 reporting indicated 14 sectors had at least 1 member that fell victim to a ransomware attack in 2021. 13

13 Accessibility description: Chart shows Infrastructure Sectors Victimized by Ransomware. Healthcare and Public Health was highest with 148 followed by Financial Services 89; Information Technology 74; Critical Manufacturing 65; Government Facilities 60; Commercial Facilities 56; Food and Agriculture 52; Transportation 38; Energy 31; Communications 17; Chemical 12; Water and Wastewater Systems 4; Emergency Services 2; Defense Industrial Base 1.
Of the known ransomware variants reported to IC3, the three top variants that victimized a member of a critical infrastructure sector were CONTI, LockBit, and REvil/Sodinokibi.
 14
14
According to information submitted to the IC3, CONTI most frequently victimized the Critical Manufacturing, Commercial Facilities, and Food and Agriculture sectors. LockBit most frequently victimized the Government Facilities, Healthcare and Public Health, and Financial Services sectors. REvil/Sodinokibi most frequently victimized the Financial Services, Information Technology, and Healthcare and Public Health sectors.
Of all critical infrastructure sectors reportedly victimized by ransomware in 2021, the Healthcare and Public Health, Financial Services, and Information Technology sectors were the most frequent victims. The IC3 anticipates an increase in critical infrastructure victimization in 2022.
The FBI does not encourage paying a ransom to criminal actors. Paying a ransom may embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and /or fund illicit activities. Paying the ransom also does not guarantee that a victim’s files will be recovered. Regardless of whether you or your organization have decided to pay the ransom, the FBI urges you to report ransomware incidents to your local FBI field office or the IC3. Doing so provides investigators with the critical information they need to track ransomware attackers, hold them accountable under U.S. law, and prevent future attacks.
14 Accessibility description: Chart shows top variants Victimizing Critical Infrastructure 2021 Incidents. REvil/Sodinokibi, Locbit, and CONTI.
TECH SUPPORT FRAUD15
Tech Support Fraud involves a criminal claiming to provide customer, security, or technical support or service to defraud unwitting individuals. Criminals may pose as support or service representatives offering to resolve such issues as a compromised email or bank account, a virus on a computer, or a software license renewal.
Many victims report being directed to make wire transfers to overseas accounts or purchase large amounts of prepaid cards. In 2021, the IC3 received 23,903 complaints related to Tech Support Fraud from victims in 70 countries. The losses amounted to more than $347 million, which represents a 137 percent increase in losses from 2020. Most victims, almost 60 percent, report to be over 60 years of age, and experience at least 68 percent of the losses (almost $238 million).

Tech support scammers continue to impersonate well-known tech companies, offering to fix non-existent technology issues or renew fraudulent software or security subscriptions. However, in 2021, the IC3 observed an increase in complaints reporting the impersonation of customer support, which has taken on a variety of forms, such as financial and banking institutions, utility companies, or virtual currency exchanges.
15 Accessibility description: Chart shows Tech Support Losses Over Past 5 Years. 2021 $347,657,432; 2020 $146,477,709; 2019 $54,041,053; 2018 $38,697,026; 2017 $14,810,080.
Table of Contents
- IC3 COMPLAINT STATISTICS
- THREAT OVERVIEWS FOR 2021
- IC3 by the Numbers
- 2021 CRIME TYPES
- Appendix A - Definitions
- Appendix B - Additional Information about IC3 Data